What is a Software Bill Of Materials ?
Where does it come from?
As the name suggests, SBOM comes from BOM or Bill of Materials. It is a list of everything that makes up a product and how the product was built. Essentially, an SBOM is a list of all the components of a software that allow it to function (libraries, packages, drivers). To delve deeper, it is actually a data exchange format, not intended to be read by humans. There are several SBOM formats, the most commonly used are SPDX (Linux Foundation) and CycloneDX (OWASP).
Why do it?
Firstly, it can help visualize the dependencies of your software and possibly sort them out. It also allows tracking potential vulnerabilities in a system. In Europe, it will become mandatory in December 2027 to be able to provide an SBOM for any software sold in the European Union. More info here: SBOM-europe, Cyber Resilience Act
How?
I will use Trivy to generate an SBOM and scan a PostgreSQL 17.4 image.
Generate an SBOM.
Here, we generate an SBOM in CycloneDX format and also generate a Vulnerability Exploitability eXchange (VEX) using the --scanners parameter.
trivy image --scanners vuln --format cyclonedx --output result.json postgres:17.4We end up with a JSON file of 29,000 lines, which is not very practical.
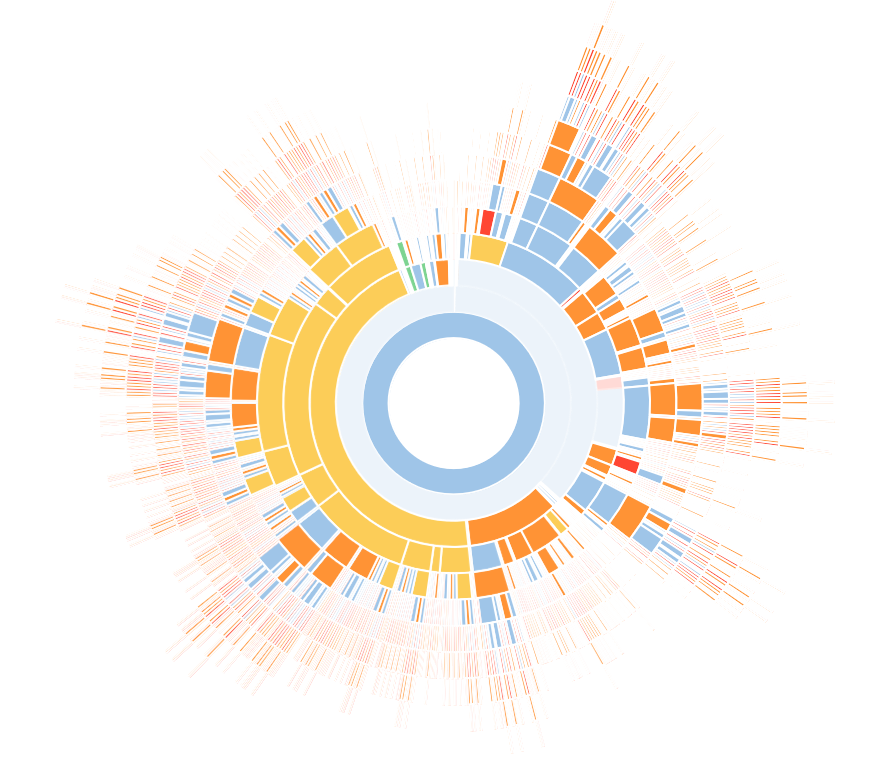
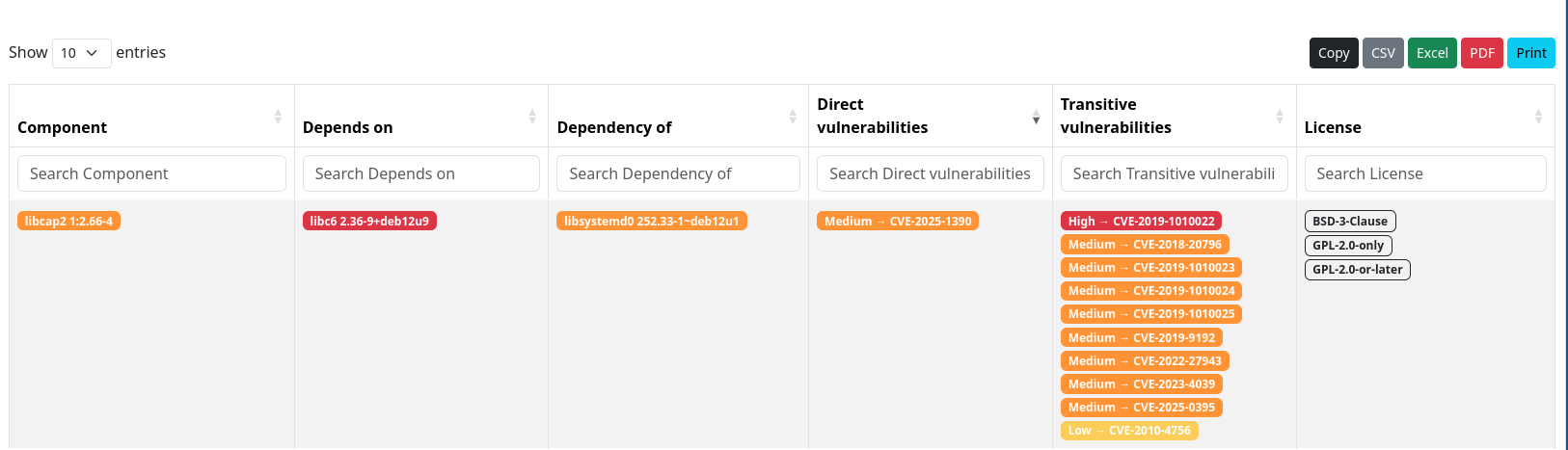
To make our SBOM readable by humans, we can use Sunshine, a tool that allows visualizing SBOMs in CycloneDX format. Sunshine will generate an HTML file containing a dependency diagram and a table listing all the components of our software.
Since we also created a VEX, Sunshine will also display the vulnerabilities of each component.
python3 sunshine.py -i result.json -o sbom.htmlExample of the generated diagram.